Incidents rarely knock before entering. One moment, your systems are humming along smoothly, and the next, an alert pierces the calm. It might be an outage, a breach, or a critical slowdown. Whatever it is, the difference between chaos and control often lies in one thing: how ready you are to respond.
An incident response runbook is that readiness, captured in writing. It’s the blueprint your team can reach for when seconds count. A structured, up-to-date runbook can turn confusion into coordination and drastically reduce Mean Time to Acknowledge (MTTA), Mean Time to Resolve (MTTR), and overall operational risk. In simple terms, an incident response runbook is a detailed, step-by-step guide that helps teams handle technical incidents quickly and consistently.
Key Takeaways
- Incident response runbooks create structure under pressure, turning confusion into clear, repeatable steps that guide teams toward fast, consistent recovery.
- Automated runbooks cut response times, helping teams reduce MTTA and MTTR through integrated tools that trigger actions the moment alerts appear.
- Accurate, regularly updated documentation builds trust, ensuring responders always follow the right process and maintain compliance with frameworks like SOC 2 and ISO 27001.
- Effective communication checklists align everyone, keeping stakeholders, engineers, and leadership informed and confident throughout the incident lifecycle.
- Continuous improvement keeps runbooks valuable, using post-incident reviews to refine steps, eliminate friction, and evolve with changing systems and risks.
What Is an Incident Response Runbook?
A runbook is more than documentation. It’s a living, tactical guide that walks responders through how to handle a specific incident, from trigger to resolution. Where a manual explains theory, a runbook provides clarity under pressure. It eliminates hesitation and ensures anyone, regardless of seniority, can take action.
In essence, an incident response runbook is your operational safety net. It can also be referred to as an incident response SOP, response checklist, or incident playbook example, depending on the organization’s structure.
Runbook vs. Playbook
In essence, an incident response runbook is your operational safety net. It can also be referred to as an incident response SOP, response checklist, or incident playbook example, depending on the organization’s structure.
| Aspect | Runbook | Playbook |
|---|---|---|
| Purpose | Tactical, step-by-step instructions | Strategic, high-level coordination |
| Focus | Fixing a specific problem | Managing overall response |
| Example | Database CPU spike | Company-wide outage or breach response |
| Owner | Engineers, on-call teams | Incident commanders, leadership |
Why Every Organization Needs Runbooks
Consistency saves minutes, and minutes save revenue. In complex environments, institutional memory and heroics are unreliable. Runbooks enforce operational discipline, especially under stress. They also help teams comply with frameworks like SOC 2, ISO 27001, and DORA, which require documented, testable incident processes.
Beyond compliance, a good runbook ensures reduced downtime, smoother handoffs, and stronger accountability during investigations. When regulators, auditors, or leadership ask for proof of control, your runbook is that proof.
The 5 A’s Framework for Effective Runbooks
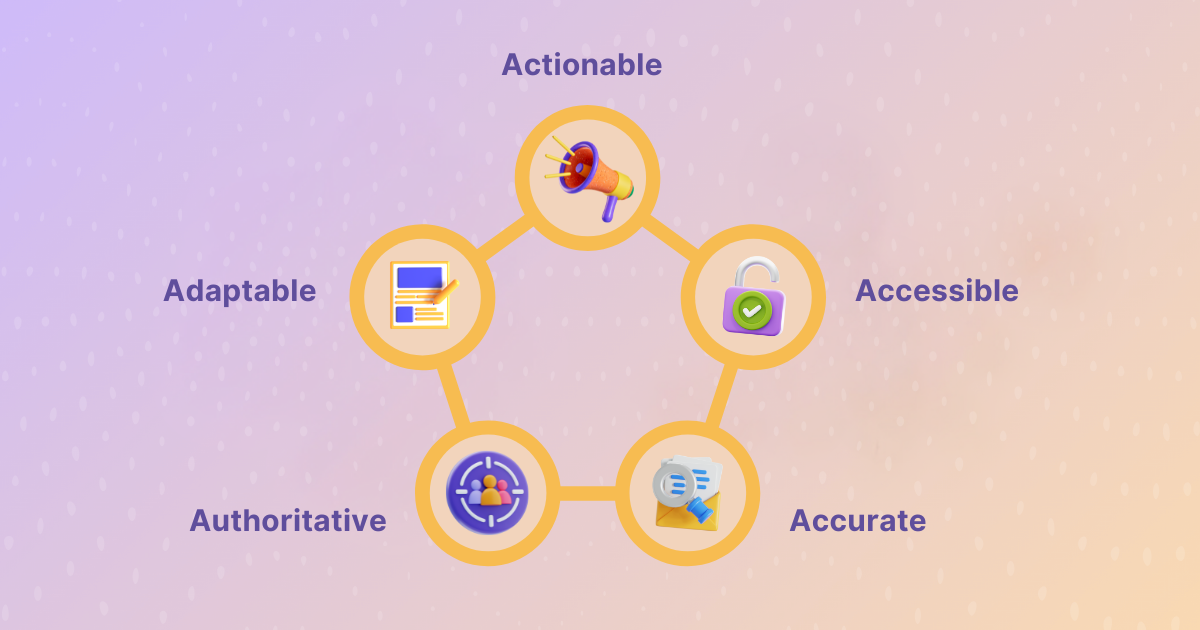
A trustworthy runbook follows five simple principles; Actionable, Accessible, Accurate, Authoritative, and Adaptable.
1. Actionable
Every step should be a command, not a paragraph. Long narratives slow decision-making and create unnecessary friction. The best runbooks can be scanned in seconds, allowing responders to move with confidence. Each instruction should be clear, direct, and impossible to misinterpret.
2. Accessible
If your runbook is buried in a wiki no one remembers, it might as well not exist. It needs to be visible where people actually work during incidents. Make sure it can be quickly found through alerts, surfaced inside Slack or PagerDuty, or automatically attached through Rootly. Accessibility should never be an afterthought when response time matters most.
3. Accurate
A single outdated command can destroy trust. Schedule quarterly reviews and make version control a standard part of your workflow. Keep ownership visible to ensure accountability. A well-maintained runbook always reflects the current and accurate state of your infrastructure.
4. Authoritative
Conflicting documents breed hesitation and slow down decision-making. Each procedure should have one clear and definitive source to avoid confusion. Make sure team members always know which document to trust in the heat of an incident. Use your incident management platform as the single home for all approved and updated versions.
5. Adaptable
Your systems evolve constantly, introducing new dependencies and risks. Your runbooks should evolve alongside them to stay relevant. Post-incident reviews offer valuable insight into what worked and what didn’t. Use that moment to update steps, refine context, and strengthen your team’s future responses.
Step-by-Step: How to Create an Incident Response Runbook
Creating a runbook is a deliberate act of empathy for your future self and your team. It’s about removing uncertainty when pressure is highest.
Step 1: Define Scope, Trigger, and Impact
Start with clarity. Identify what alert activates the runbook and which service or SLOs it affects. For instance, a “Database-High-CPU” runbook should state its trigger conditions, impact radius, and ownership. This context gives responders immediate understanding of what’s at stake.
Step 2: Collect Context Automatically
When incidents strike, responders shouldn’t scramble for logs or dashboards. Automate the process of collecting relevant context. Use tools like Rootly to pull metrics, deployment histories, and monitoring links directly into the incident channel. Having this data instantly available saves precious minutes and gives engineers immediate clarity on where to act first.
Step 3: Build a Quick Triage Checklist
Triage determines severity fast. A good runbook includes simple yes/no questions:
| Question | Action Owner | Severity |
|---|---|---|
| Is more than 10% of traffic affected? | On-call engineer | SEV-1 |
|
Any data loss detected? |
Security lead | SEV-1 |
| Is the issue isolated to one region? | DevOps |
SEV-2 |
Step 4: Document the Exact Fix
The heart of a runbook is precision. Commands should be simple, reliable, and copy-pasteable to avoid errors. Each step must be verified to ensure consistency in every situation. Never assume memory works well at 3 a.m., because if you can’t paste it, it’s not production-ready.
Step 5: Include a Communications Checklist
- Clear communication prevents confusion, especially when multiple teams are involved.
- Every update must be timely, specific, and easy to follow so that no one is left guessing.
- Keep a concise checklist to maintain alignment throughout the process.
- Update the incident Slack channel, post on the status page, and notify stakeholders or leadership immediately.
Step 6: Verify Resolution
Data proves success. Always measure outcomes instead of relying on assumptions. Define exact metrics such as latency below 200ms, error rate under 0.5%, or successful API health checks. Avoid subjective language like saying “it feels faster,” and depend on hard evidence instead.
Step 7: Close the Loop
Once resolved, guide the wrap-up carefully to ensure no detail is overlooked. Schedule a post-mortem to capture lessons learned while they are still fresh. Assign follow-up tasks to address root causes and prevent recurrence. Update the runbook with new insights so that each incident makes your playbook stronger.
Incident Response Runbook Templates (Copy & Customize)
1. Generic Incident Response Runbook Template
A comprehensive template designed to adapt to any incident type:
| Section | Actions |
|---|---|
| Trigger & Detection | Describe what initiates this runbook, the monitoring tool involved, and relevant alert conditions. |
|
Impact Assessment |
Outline which systems, services, or users are affected and how severity is determined. |
| Containment Actions | Specify immediate steps to prevent escalation and protect data integrity. |
| Resolution Workflow | Include detailed, copy-pasteable commands, scripts, and rollback instructions. |
| Validation & Verification | Define measurable success criteria such as performance thresholds or restored availability. |
| Communication Plan | Detail how to update internal channels, status pages, and external stakeholders. |
| Post-Incident Review | Capture root cause, lessons learned, and follow-up actions for continuous improvement. |
2. Security Breach Runbook Template
For compromised credentials or phishing attempts:
| Section | Actions |
|---|---|
|
Detection & Identification |
Verify indicators of compromise through monitoring tools, unusual login attempts, or phishing reports. |
|
Containment |
Immediately isolate affected accounts, revoke all active tokens, and disable compromised sessions. |
| Eradication | Rotate passwords and keys, patch exploited vulnerabilities, and audit access logs for lateral movement. |
| Communication & Escalation | Notify the security and legal teams, document findings, and prepare internal and external communication drafts. |
| Post-Incident Validation | Confirm threat removal, re-enable accounts under stricter policies, and conduct a brief awareness session to prevent recurrence. |
3. Cloud Outage Runbook Template
When AWS or another provider experiences downtime:
| Section | Actions |
|---|---|
|
Detection |
Confirm outage through the provider’s status dashboard or monitoring alerts. |
|
Assessment |
Identify which services or regions are impacted and determine user-facing effects. |
| Mitigation | Redirect traffic to secondary regions or backup infrastructure if available. |
| Stabilization | Enable read-only or degraded modes to maintain limited functionality. |
| Communication | Post clear updates on internal and public status pages, keeping users informed. |
| Validation | Continuously monitor recovery metrics, re-enable services gradually, and document lessons learned for future improvement. |
4. Database Performance Runbook Template
For slow queries or CPU spikes:
| Section | Actions |
|---|---|
|
Identification |
Locate problematic queries or resource bottlenecks using database monitoring tools. |
|
Remediation |
Restart affected nodes, optimize queries, or reallocate resources as required. |
| Optimization | Clear cache, rebuild indexes, or reset connection pools to stabilize performance. |
| Validation | Track latency and CPU metrics post-action to confirm improvement and sustained stability. |
5. Customer-Facing Downtime Runbook Template
When user-facing systems go offline:
| Section | Actions |
|---|---|
|
Public Acknowledgment |
Announce the outage promptly across official channels to maintain transparency and trust. |
|
Incident Page Updates |
Provide frequent, clear updates on the incident status page to inform users of progress. |
| Customer Communication | Alert customer support teams with current details so they can respond accurately to user inquiries. |
| Verification & Resolution | Validate the fix with performance metrics and monitoring before publicly declaring full resolution. |
Real-World Examples of Incident Response Runbooks
Example 1: TripAdvisor: Cross-Team Coordination
TripAdvisor’s engineering teams use standardized runbooks to synchronize communications during global outages. Technical and non-technical updates flow through clear channels, ensuring users stay informed and engineering stays focused.
Example 2: Hypothetical Example: Database Outage
Imagine a database cluster degradation at peak hours. The runbook identifies the alert, isolates affected shards, performs health checks, and initiates failover procedures. Each command is validated, each update communicated. What once caused confusion now runs like choreography.
Example 3: Security Runbook for Ransomware
This scenario outlines a ransomware response:
- Isolate impacted systems immediately
- Disable compromised credentials
- Communicate with internal stakeholders
- Contact legal and security authorities
- Begin restoration from secure backups
Keeping Runbooks Up to Date

Runbook Lifecycle Management
A runbook’s value depends on its freshness and consistent upkeep. Store them in Rootly to ensure transparency and easy collaboration. Apply proper version control and make ownership clearly visible for accountability. Automate quarterly reminders to guarantee that every runbook remains accurate and trusted when needed most.
Review and Improve
Every incident offers valuable lessons that should be captured while details are still clear. Update runbooks immediately after each post-mortem to reflect what worked and what didn’t. Review patterns from MTTR and escalation data to identify areas needing refinement. Applying these insights ensures that your runbooks evolve with your systems and continue driving faster, more accurate responses.
When to Retire a Runbook
If a system is deprecated or replaced, make sure its runbook is properly archived and documented. Removing outdated materials prevents confusion and keeps your repository focused on active systems. Regular cleanup of old runbooks shows operational discipline and supports faster discovery during incidents. Maintaining only relevant, updated documents builds lasting trust across your teams.
How to Automate Incident Response Runbooks
Automation Benefits
Automation removes friction from the entire response process. It reduces human error, cuts triage time, and lessens on-call fatigue while keeping teams aligned. With automation, repetitive manual tasks become predictable, freeing engineers to focus on problem-solving. The future of incident response lies in automated incident response runbooks that can execute diagnostics, rollbacks, and recovery workflows instantly.
Integrations and Tools
Tools like Rootly make automation accessible to teams of all sizes. Each platform supports different workflows and levels of integration flexibility. Many use intuitive no-code or low-code triggers that make it simple to connect alerts directly to automated responses. This flexibility empowers organizations to streamline their incident process without needing extensive development effort.
Examples of Automation in Action
- Auto-assign roles and channels
- Auto-update the status page
- Pre-fill stakeholder communication drafts
Compliance, Security, and Audit Readiness

How Runbooks Support SOC 2 & ISO 27001
Auditors love proof, and runbooks provide exactly that. They create traceability across every action taken during a response, ensuring accountability at every stage. Each step becomes verifiable evidence that processes are documented, repeatable, and executed with consistency. This transparency builds confidence among auditors, regulators, and leadership alike.
DORA and SEC Disclosure Rules
Modern compliance regimes demand rapid disclosure and full accountability from every organization. Teams must be able to show not just speed, but transparency in how incidents are handled and communicated. Documented response workflows reveal the maturity of operational processes and readiness under pressure. This level of structure builds confidence among auditors, stakeholders, and customers alike.
Incident Documentation Best Practices
Capture every detail such as timestamps, version numbers, and response owners to ensure full visibility. Documentation should leave no room for ambiguity when reviewing incident history. Accountability becomes easier when every step is clearly recorded and attributed. Clear records transform confusion into clarity and allow teams to analyze performance confidently.
Common Pitfalls to Avoid
- Outdated or duplicate runbooks
- Overly complex or narrative instructions
- Missing ownership or unclear responsibility
- Neglecting communication workflows
- Failure to link runbooks directly to alert systems
Key Metrics to Track for Incident Response Runbooks
Measure what matters. These metrics define success:
- MTTD (Mean Time to Detect) – How quickly you notice incidents.
- MTTA (Mean Time to Acknowledge) – How long it takes to respond.
- MTTR (Mean Time to Resolve) – How fast you fix the issue.
- Incident Volume & Severity Rate – Frequency and impact.
- SLA Compliance & First-Touch Resolution – How often commitments are met.
These indicators show not just performance but the health of your response culture.
Why Modern Teams Trust Runbooks to Lead Under Pressure
Every incident is a test of resilience. When alarms go off and adrenaline spikes, clarity becomes your strongest weapon. Well-built runbooks transform that chaos into order. They remove ego, guesswork, and fear, leaving only precision. Over time, they evolve into your most valuable operational asset, a mirror reflecting lessons learned from every challenge.
At Rootly, we’ve seen how automation and documentation together can transform incident management. Our goal is to help teams not just survive crises but lead through them. With structured, automated runbooks, we empower organizations to move from firefighting to foresight.
Frequently Asked Questions
1. What’s the difference between a runbook and a playbook?
A runbook is a tactical, step-by-step checklist to fix a specific technical problem. A playbook is a high-level, strategic guide that defines how your people and organization respond to any incident, covering roles, communication, and escalation policies.
2. How detailed should a runbook be?
It should be detailed enough that a new engineer can successfully execute it at 3 a.m. under pressure. Prioritize clarity and scannability with copy-pasteable commands and checklists over long paragraphs.
3. Can runbooks be automated?
Yes, and they should be. Modern incident tools can automatically trigger a runbook from an alert and execute scripted actions like diagnostics or rollbacks. This is key to resolving common issues instantly and reducing on-call fatigue.
4. Where should we start if we have no runbooks?
Don't try to document everything at once. Start by creating runbooks for the 2-3 incidents that are either the most frequent (to reduce weekly toil) or the most impactful (your big, customer-facing outages).
5. How do you keep runbooks from getting outdated?
Treat them like code. Store them in a central, version-controlled system like Git or an incident management platform. Review them after every major incident they're used in and schedule automated reminders for owners to verify them quarterly.
6. Are runbooks required for compliance like SOC 2?
Yes. Frameworks like SOC 2, ISO 27001, and DORA require you to have documented and testable incident response processes. Well-maintained runbooks are the most direct way to provide auditors with the evidence they need.














